Cato Networks Demonstrates AI-Based Policy Analysis and Enforcement at AWS Summit Tel Aviv 2025
|
Listen to post:
Getting your Trinity Audio player ready...
|
The Hidden Risk in Security Policies
Policy misconfigurations remain one of the most common and costly risks in network security. Studies in recent years have shown that the vast majority of firewall breaches stem from policy configuration errors, and human mistakes or skill gaps continue to be a leading cause of major security incidents. Traditionally, organizations either wait for a breach or an audit to detect issues, both of which are reactive approaches.
NIST warns that policy misconfigurations can enable unauthorized access. MITRE ATT&CK techniques like T1046 (Network Service Discovery) and T1562 (Impair Defenses) show how attackers exploit them.warns that policy misconfigurations can enable unauthorized access. MITRE ATT&CK techniques like T1046 (Network Service Discovery) and T1562 (Impair Defenses) show how attackers exploit them.
In response to this growing challenge, Cato Networks announced a new AI-driven capability on May 13, Cato Autonomous Policies, with the first use case being Autonomous Policies for FWaaS. This new solution continuously uncovers policy misconfigurations by analyzing the intent behind policy rules, not just their syntax, and puts enterprises in control, enabling a more proactive and continuous approach to their Zero Trust strategy. Naor Kalbo (principal researcher, Cato Networks), Meidan Nasi (solutions architect, AWS), and Yazan Khalaf (solutions architect, AWS) will present this breakthrough and its impact on firewall policy management in a talk at AWS Summit Tel Aviv 2025 on May 28 at 11:45 AM IST in Pavilion 10 – Hall B. (While you’re there, join us for two other sessions including a fireside chat with Cato Networks CEO Shlomo Kramer. More details can be found here.)
From Static Checks to Smart Context
Legacy policy enforcement typically relies on manual reviews, posture scores, and static rule evaluations, which are difficult to scale in today’s dynamic and complex environments. With thousands of overlapping firewall rules created to meet real business needs, security teams often struggle to identify which rules are obsolete, temporary, or misconfigured. The risk of disrupting critical services frequently results in unused or overly permissive rules being left in place.
Cato Autonomous Policies for FWaaS addresses this challenge with a multidimensional approach. By leveraging AI to analyze the intent behind rules, including sentiment elements such as rule names, descriptions, and behavioral patterns, Cato Autonomous Policies for FWaaS identifies policy misconfigurations that traditional tools overlook. Traditional policy configuration analysis has reached its limits. It often misses subtle but important signals hidden in text-based, context-rich data. Cato Autonomous Policies for FWaaS operates proactively and continuously and is designed to meet the realities of modern, large-scale network environments.
Firewall-as-a-Service (FWaaS) | Visit our pageInside the Innovation: How It Works
Cato Autonomous Policies for FWaaS is part of the Cato SASE Cloud Platform. The new approach to identifying policy misconfigurations goes beyond simple detection by interpreting intent, identifying anomalies, and assessing risk in ways that traditional tools are not equipped to handle. Cato Autonomous Policies for FWaaS leverages Amazon Bedrock to continuously analyze not only rule configurations, but also the intent behind them by interpreting metadata such as rule names and free-text descriptions. This approach enables the identification of policy misconfigurations that are typically missed by traditional tools. As a result, we enable more accurate and efficient detection of unused, obsolete, or overly permissive rules, without increasing the operational burden on security teams.
In Figure 1, we illustrate the system architecture and how we apply contextual AI analysis across policy layers to uncover policy misconfigurations that traditional tools often miss.
Figure 1. AI-powered engine analyzing policy misconfigurations
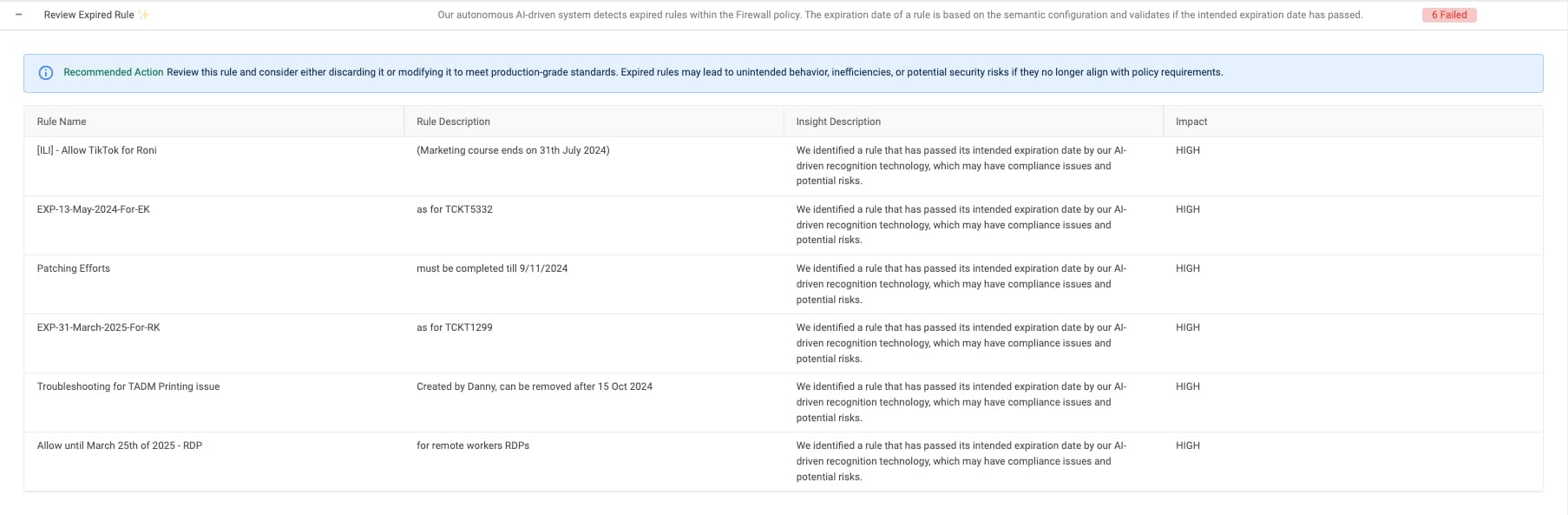
In Figures 2 and 3, we show examples where temporary or expired rules created for past business needs were flagged. These rules had been forgotten or overlooked among thousands of others and have now surfaced for action.
Figure 2. Identified temporary rules with risky overexposure and suggested actions
Figure 3. Identified expired rules with risky overexposure and suggested actions
This is just a sneak peek at what’s coming. We will demonstrate the full capability of Cato Autonomous Policies for FWaaS at AWS Tel Aviv Summit 2025. We look forward to seeing you there.